Articles
Secure remote VM access with Azure Bastion and vNet peering
Azure Bastion is a platform-managed PaaS service that allows you to connect to a virtual machine using your browser and the Azure portal. It provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal...
Provide access to your Key Vault with Azure role-based access control (RBAC) now
Key Vault access policies allow you to set very specifically what rights an identity has on keys, secrets, and certificates. However, you have to set this per key vault, and you cannot use the resource hierarchy within Azure (e.g. Management...
Enforce or audit Key Vault requirements of certificates, secrets, and keys by leveraging Azure Policy
During discussions about Azure security, Azure Key Vault is regularly discussed. More and more organizations are aware that sensitive data such as secrets and keys can be stored here, while other resources can make use of it. But also the next...
Disable specific Azure Defender vulnerability assessment findings
Azure Defender includes vulnerability scanners to scan images in your Azure Container Registry and your virtual machines. Sometimes there is an organizational need to ignore a finding, rather than remediate it. Risks may have been lowered because...
Create an exemption rule to exclude a resource from a security recommendation
A core priority of any security team is to ensure that the analysts can focus on the tasks and incidents that are important to the organization. Security Center has many features for customizing the information that you give the most priority to...
Azure Security Center Standard rebranded to Azure Defender
Azure Security Center (ASC) is the center of many security-related features that are present within Azure. You can gain insight into the security status of your environment from 1 portal. Think of, for example, continuous assessments, regulatory...
Azure Active Directory Continuous Access Evaluation
Token expiration and refresh is a standard authentication mechanism and widely used across the industry. When a client application (like Teams) connects to a service (like SharePoint Online), the API requests are authorized using OAuth 2.0 access...
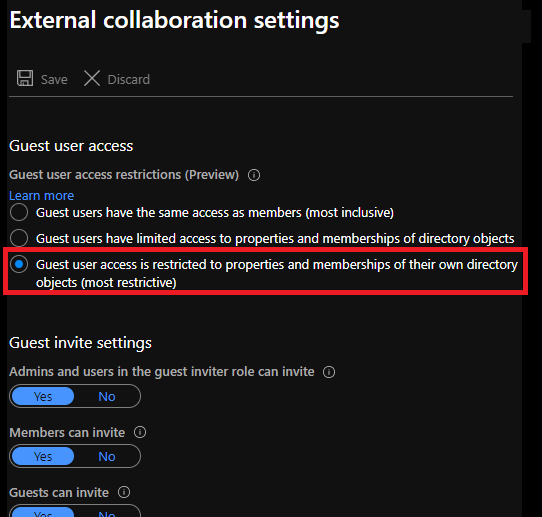
Restrict access permissions for Azure Active Directory guest users
When a user is added within Azure AD, they are automatically assigned a certain permission set. There is a difference in the origin of the user here. There are 2 options: A user from your own organization (from the same tenant), called a member...
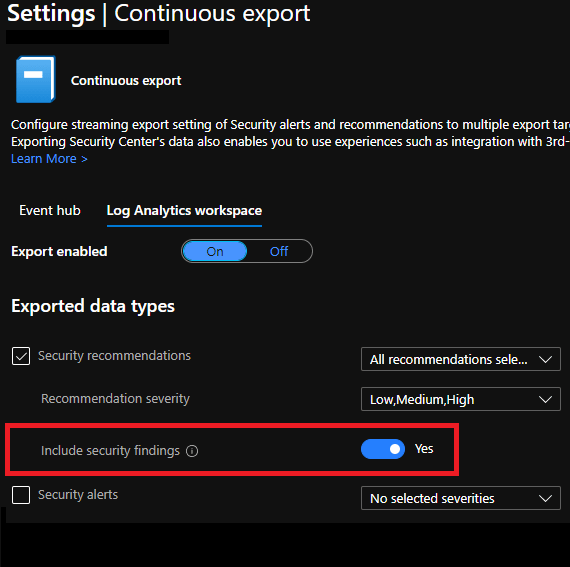
Continuous Export of Nested Recommendations
Security Center periodically analyzes the security state of your Azure resources to identify potential security vulnerabilities. It then provides you with recommendations on how to remediate those vulnerabilities. Recommendations are actions for...
Enforcing Azure Security Center recommendations when creating new resources
With the recent Azure Security Center updates from September, it now has the ability to help prevent misconfigurations of new resources with regard to specific recommendations. This feature can help keep your workloads secure and stabilize your...